https://www.exploit-db.com/exploits/22547在这个链接看到了一个正则匹配绕过,不知道原理。感觉给出的payload中依然存在"O:"字符会被匹配到,自己实验了一下也会被匹配到,不知道是如何进行绕过的,可以请大佬讲解一下吗?
static public function safeUnserialize( $serialized )
{
// unserialize will return false for object declared with small cap o
// as well as if there is any ws between O and :
if ( is_string( $serialized ) && strpos( $serialized, "\0" ) === false )
{
if ( strpos( $serialized, 'O:' ) === false )
{
// the easy case, nothing to worry about
// let unserialize do the job
return @unserialize( $serialized );
}
else if ( ! preg_match('/(^|;|{|})O:[0-9]+:"/', $serialized ) )
{
// in case we did have a string with O: in it,
// but it was not a true serialized object
return @unserialize( $serialized );
}
}
return false;
}
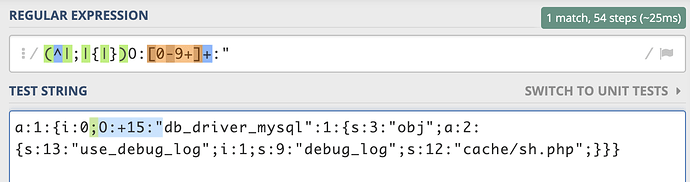
看else if 的这个case的条件 = > O:[0-9]+:
然后用 O:+15
1 个赞
大哥你这是你自己带了+号,别人code snippet里面没有啊? 能仔细看看不
对不起😂是我蠢了,多谢师傅解答
https://github.com/MegadodoPublications/exploits/blob/master/composr.md 看看这个,非常有趣哦,可能会给你带来新思路,上面这个绕过7.2以后就不行了 )